The SNS JU HORSE project studies how to exploit 5G concepts to define what 6G networks will be like, introducing the new paradigms of digital twins and Artificial Intelligence.
The world is currently experiencing the deployment of 5G networks. This promises a revolutionary approach to integrate the advantages of software-defined networking and cloud-native network function virtualisation within the fabric of mobile networks. This is expected to foster an evolution toward disaggregation, new software-based paradigms in architecting and operating future connectivity platforms, and the embracement of computing, automation, smartness, trust, privacy, and security features. Nevertheless, 5G is only paving the way.
It is expected that 6G will be the mobile network to fully develop such concepts into an advanced, disaggregated, virtualised and multi-vendor infrastructure. It will challenge the security and resilience design to the next level, and by managing the (currently) unknown, complex, and highly versatile infrastructures as they evolve.
The SNS JU HORSE project (Holistic, Omnipresent, Resilient Services for Future 6G Wireless and Computing Ecosystems) is a research project that aims to study architectures and modules for the 6G mobile networks.
HORSE aims at defining a novel human-centric, open-source, green, sustainable, coordinated provisioning and protection evolutionary platform, which can inclusively yet seamlessly combine advancements in several domains as they get added to the system. The envisioned scenario can be summarised in Fig. 1.
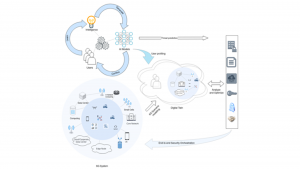
The project is coordinated by Consorzio Nazionale Interuniversitario per le Telecomunicazioni (CNIT) and involves 14 partners across Europe (Fig. 2). It is funded for around €7m in the framework of the Smart Networks and Services Joint Undertaking (SNS JU) initiative for 2023-2025, and it consists of a series of projects that define Phase 1 of 6G design. The project coordinator is Prof Fabrizio Granelli, a Professor at the University of Trento and Member of the CNIT Research Unit in Trento, Italy.
The European Smart Networks and Services Joint Undertaking (SNS JU) is a public-private partnership to facilitate and develop industrial leadership in Europe in 5G and 6G networks and services. It funds projects that shape a solid research and innovation (R&I) roadmap and deployment agenda by engaging a critical mass of European stakeholders and facilitating international cooperation on various 6G initiatives.

The HORSE project focuses on a holistic research approach aimed to design, develop, and validate an autonomous, self-evolving and extendable 6G-ready architecture providing a human-centric approach to security workflows by enabling top-down, bottom-up, and end-to-end security solutions.
The key challenges HORSE addresses in the 6G landscape are outlined in Fig. 3.
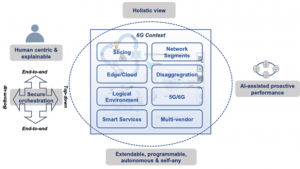
Technical challenges and contribution to 6G
HORSE promises to go beyond the state of the art and to propose the following progress:
Developing security framework for 6G systems
HORSE will significantly advance the state of the art by designing and developing a holistic, human-centric, sustainable security framework for end-to-end 6G systems, securing the lifecycle management at multiple levels in multi-stakeholder and multi-domain resource environments.
HORSE will provide intent-based orchestration functions to automate processing, storage, and management by mapping specific security intents using advanced AI/ML algorithms into security and reliability actions and policies spanning multiple heterogeneous domains.
In addition, HORSE will include predictive threat detection and mitigation procedures based on AI/ML techniques to protect 6G systems from attacks that can potentially impact the performance or availability of the service as well as data privacy, with a special focus on tasks that might potentially discover habits, gender/political/religious inclination, social and personal relationships, medical, or other sensitive data.
Implementing an AI Secure and Trustable Orchestration component
HORSE will significantly extend the state of the art by developing a security framework that will provide end-to-end security and trust in multi-stakeholder resource environments.
HORSE will implement an AI Secure and Trustable Orchestration (STO) component to increase the reliability, trust, and resilience of virtualised environments. Such a component will include an end-to-end secure connectivity manager that will provide service orchestration, support recursive deployment with high device heterogeneity in virtualised scenarios, and end-to-end resource self-configuration provisioning a secure framework spanning multiple domains.
The STO will also include a domain orchestrators connector that will provide trustworthy connections across multiple domains using trusting execution environments based on distributed ledger technology and a cross-domain VNF licensing management service to control the utilisation of licensed VNFs across multiple domains.
In addition, HORSE will also provide a trustable AI engine that will oversee and ensure that all deployed services run in a secure environment by means of trustworthy, enhanced federated learning techniques.
Altogether, the HORSE security framework will solve some of the security challenges of the O-RAN specification, focusing on securing the interfaces and ensuring a secure O-RAN operation in untrusted clouds.
Identifying specific cyber threats to the 6G landscape
HORSE proposes to identify and attack the specific threats the 6G landscape is sensitive to, using and extending the work done in the MITRE ATT&CK Framework, defining the attributes and parameters needed to develop such characterisation successfully.
Moreover, the work aims not only to characterising such threats, but also to contribute to the cyber security community by identifying new possible attack vectors, proposing novel predictive strategies, detection measures and mitigation solutions. These will strengthen the 6G landscape cyber security, while also spreading out knowledge on potential attacks and corrective measures within the involved community.
Enhancing the future of green 6G
HORSE will mark progress in green networks by identifying the required tools and paradigms to enhance the performance of future green 6G and reduce energy consumption.
HORSE will contribute to achieving high energy efficiency for resource-constrained devices in future 6G networks by using new materials and improving the efficiency of energy harvesting technologies. This will lead to a sustainable green network.
In short, HORSE addresses this challenge by proposing a battery-free, energy-efficient, low-cost computing and sensing infrastructure for future 6G networks.
Integration of digital twins
HORSE aims to investigate networking and resource management solutions by considering the specifications of digital twins’ different services.
HORSE will address the integration of DTs in future communications systems and their implications on network management aspects related to resource allocation and lifecycle management.
HORSE will exploit the great potential for optimising the utilisation and integration of DTs using AI/ML methods. Suitable DT module composition and abstraction level play a crucial role in realising an overall secure system, decreasing the computation delay and energy consumption.
One of the key objectives is to identify the required AI/ML functions and the suitable composition within each DT network model. This could be done using online and offline approaches such as reinforcement learning and supervised learning.
AI approach for greater security in 6G networks
HORSE will provide a distributed AI/ML approach for security enhancement in 6G networks closer to the data source of interest. In this context, implementing federated learning (FL) represents a major goal towards service disaggregation and security optimisation. Based on FL, data selection and training will be performed locally, an approach that obviously protects data privacy and offers a considerable reduction of the overhead/latency as a side positive effect.
Moreover, HORSE will leverage a distributed hierarchical ML structure to prevent data privacy from being compromised while targeting system disaggregation and secure optimisation. HORSE will go beyond the state-of-the-art in deep reinforcement learning methods by applying FL and meta-learning (AutoML) methods to meet policies for Trustworthy AI and improve security strategies.
Integrating intent-based networking with future 6G networks
HORSE will address the new challenges of integrating intent-based networking (IBN) with future 6G networks to facilitate user engagement and explainability. This adds more complexity regarding implementing IBN while reducing the burden for administrators.
Moreover, the ‘human-in-the-loop’ features will impose more challenges to translating future users’ intents into network configurations and operations. Simultaneously, the placement of virtual functions needs to be improved to meet the new demands provided by the 6G environment.
Deployment, optimisation, and continuity of IBNs are the main research directions that should be improved and discovered.
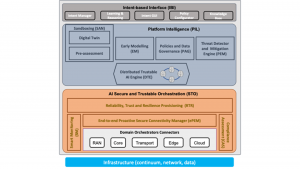
Progress on the below areas will lead to the design and deployment of the HORSE functional architecture, presented in Fig. 4:
- The domain orchestrator connectors is responsible for the proper orchestration of all
tasks related to infrastructure elements, access to the medium, transport, core, edge, and cloud. The respective sub-module handles each orchestration process to facilitate architectural deployment; - The smart monitoring (SM) component is responsible for collecting data from various and diverse domain resources and data related to the usage of the resources involved in the lifecycle management of 6G services. To this end, a dynamic analysis of performance, reliability, and security based on monitoring information will determine and optimise, among others, the required resources on the NFV infrastructure and accordingly adapt the functions of failure protection, security, or recovery methods;
- The compliance assessment (CAS) ensures that all enforced security policies and solutions generated by the trustable AI engine are in alignment with the considered regulatory framework;
- The end-to-end (E2E) secure connectivity manager (ePEM) is in charge of service orchestration, which supports recursive deployment of many functional components for multi-tenancy, high device-heterogeneity through virtualisation, E2E resource self-configuration, and most importantly, the provision of a secure framework that can span across multiple domains and applications. In the upper layer, various advanced services and applications (e.g., V2X communications) are deployed by instantiating different slices per service;
- The reliability, trust and resilience provisioning provides the tools and technologies to ensure a secure performance. The set of actions from this component will feed the ePEM with the actions to be done;
- As part of the PIL module, the distributed trustable AI engine (DTE), which runs in parallel with the executed applications, ensures that all deployed services run in a secure, distributed and optimised environment;
- The early modelling (EM), sandboxing (SAN), threat detector and mitigation engine (PEM), and the policies and data governance (PAG) will become the intelligence component HORSE relies on to predict and assess the actions to be forwarded to lower layers for secure resource orchestration and secure services deployment; and
- The intent-based interface (IBI) is responsible for mapping high-level intents into security workflows able to react to security threats and vulnerabilities, which will use AI for intent optimisation.
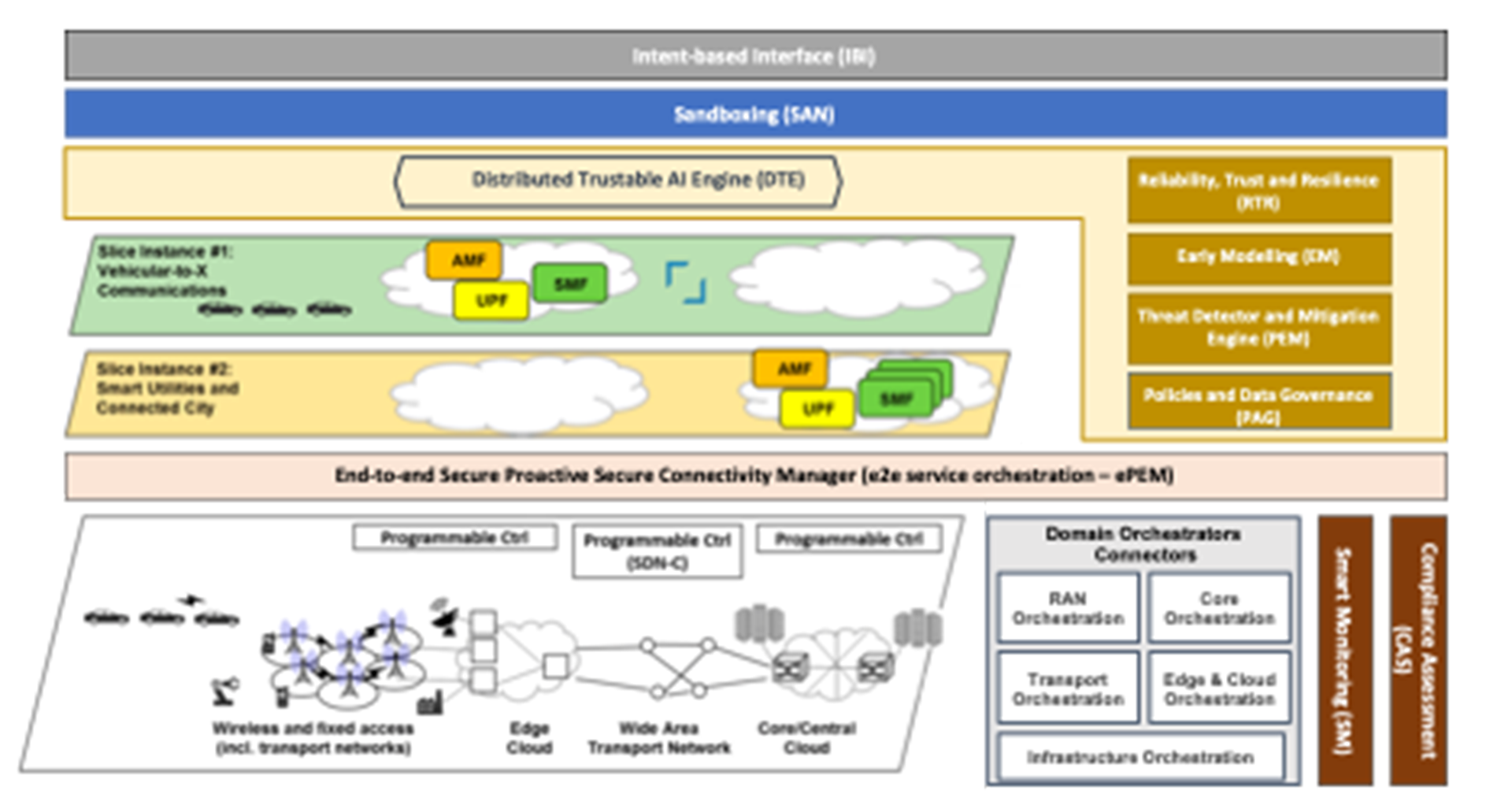
The modules developed by HORSE will seamlessly integrate within the future mobile network architecture as depicted in Fig. 5.
Impact on standardisation
HORSE will base its work on existing and emerging standards of any nature, including specifications of standardisation bodies and open-source communities. The project will seek all kinds of collaboration, from direct contributions to specifications or code bases to applicability statements and proof-of-concept demonstrators, to assess the viability of proposed solutions.
Several ETSI industry specification groups (ISGs) are targets for future project contributions, either in the form of direct content for their specifications and reports, or by means of PoC-based (proof-of-concept) analysis of their specifications.
In particular, MEC (the reference group on edge technologies), NFV (focused on network function virtualisation orchestration, management, security and reliability), ENI (dedicated to exploring data-intensive, policy-based, AI-enabled network management techniques), ZSM (to define an architecture and interoperability framework for network service total automation), and SAI (where security implications of applying AI are being considered) are the most promising objectives.
Within 3GPP, SA3 (focused on security) and SA5 (with management aspects as a goal) will be considered to bring results to impulse the evolution of the current 5G standards these groups are developing.
Moreover, ITU-T FGAN, the focus group on autonomous networks, will constitute an interesting target for combining technical and policy contributions. In policy, partners will leverage their participation in industry associations and pre-standardisation groups such as GSMA and NMRG.
HORSE project is funded by the Smart Networks and Services Joint Undertaking (SNS JU) under the European Union’s Horizon Europe research and innovation programme under Grant Agreement No 101096342.
Please note, this article will also appear in the sixteenth edition of our quarterly publication.










