CardLab Aps explores the risks of quantum computing and sustainable solutions that will help uphold online security.
Quantum computing is no longer a distant possibility; it is rapidly evolving into a practical reality with the potential to revolutionise many sectors. One area of particular concern is the impact quantum computing will have on online security.
Quantum computers, leveraging their immense processing power, can solve complex problems much faster than classical computers. While this presents great opportunities, it also introduces significant threats to online security, as these systems will be able to break existing cryptographic algorithms that form the backbone of our current digital infrastructure.
In this article, CardLab addresses the imminent risks that quantum computing poses and explores effective strategies to mitigate these threats. Specifically, we will focus on offline biometric authentication devices, which offer a convenient, sustainable solution for secure identity verification and data transmission.
Incorporating offline elements introduces a layer of complexity that undermines the straightforward processing power and mathematical logic quantum computers rely on to break cryptographic algorithms.
Understanding these evolving challenges and solutions is crucial to maintaining critical infrastructure security and trust between the infrastructure actors.
The threat of quantum computing to current cryptography
Cryptography relies on the difficulty of certain mathematical problems, such as prime factorisation, to secure information. Today’s most common cryptographic algorithms, such as RSA and ECC (elliptic curve cryptography), depend on the assumption that solving these problems takes too long for any classical computer to complete in a reasonable amount of time.
However, quantum algorithms, like Shor’s algorithm, could break these cryptosystems by exponentially reducing the time required to solve them.
In practice, this means that RSA encryption keys could be broken by quantum computers within minutes or seconds—potentially exposing sensitive information, such as financial transactions, classified data, and personal identities, or enabling account takeover or infrastructure control by bad actors.
State actors and quantum computing
While private enterprises and academic institutions are in charge of quantum research, state actors pose the most significant threat when exploiting quantum technology for cyberwarfare. Once mature, quantum computers could give governments the ability to break virtually any encryption currently in use, exposing everything from military secrets to citizens’ sensitive personal information.
State-sponsored hacking campaigns have become more common in recent years, with governments targeting other nations’ infrastructure, intellectual property, and sensitive data. With the advent of quantum computing, the capabilities of state actors will be exponentially magnified.
These governments, with almost unlimited resources, will have the power to compromise communications, financial systems, and energy grids and even manipulate elections or launch misinformation campaigns. Any organisation still relying on traditional cryptographic methods will face severe vulnerabilities.
Post-quantum cryptography: Preparing for the threat
In response to this looming threat, researchers are actively working on post-quantum cryptography (PQC), which involves algorithms designed to resist quantum attacks. PQC operates on mathematical problems that even quantum computers cannot easily solve.
However, as cryptography is built on logic chains, it can also be broken by logic, and it will be a continuous race against hackers and machine learning tools.
Organisations such as the National Institute of Standards and Technology (NIST) have been in charge of standardising these algorithms.
However, widespread implementation of post-quantum cryptography is still years away, meaning organisations need solutions today to secure their systems while these technologies mature. As CardLab has assessed, this interim period will also mean hacker skills and tools get better and faster, which could create a status quo situation once quantum cryptography has matured.
The role of offline biometric authentication devices
At CardLab, we see that a critical, sustainable solution to quantum threats is the use of offline biometric authentication devices and identity tokenisation.
These devices are designed to secure user identities and communications without relying on vulnerable network-based cryptographic protocols. They can provide offline tokenisation, adding an unknown element to the encrypted information, making hacking almost impossible.
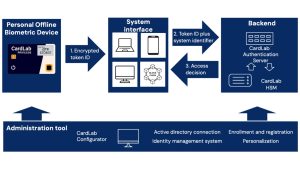
How offline biometric devices work
An offline biometric authentication device operates in a secure, isolated environment, reducing the risk of network-based attacks, including those posed by quantum computers. Here’s a breakdown of how these devices work:
- Biometric capture: The device authenticates the user using a biometric factor, a fingerprint sensor. Unlike passwords or PINs, biometrics are inherently unique and eliminate the need to remember anything. In the experience of our partner Fingerprint Cards AB, we found that secure fingerprint sensors offer significant reliability and resistance to tampering and spoofing.
- Tokenisation of identity: After biometrically verifying the user, the device generates a token representing the user’s identity. This token is event and time-sensitive and secure, meaning it can only be used for a single session within a given timeframe.
- Offline operation: Operating offline means the device does not rely on network communications during the identity verification phase and for the majority of its functions, which makes it immune to real-time interception by quantum algorithms.
- Back-end verification: Once the token is generated, it is transmitted to a secure back-end server where the identity verification is completed. The server can employ post-quantum cryptographic algorithms to ensure that even if intercepted, the token is quantum-resistant.
Advantages of biometric authentication in a quantum era
- Quantum-resistant authentication: When using secure algorithms, biometric data cannot be easily duplicated or forged, making it an ideal authentication method in a post-quantum world. Unlike traditional passwords or cryptographic keys, biometric data is inherently tied to the individual and offers a layer of protection that quantum computers cannot easily compromise as the mathematical logic is broken by the added token. This is shifting identification from a device-based model to a needed person-centred approach, as CardLab’s biometric solutions demonstrate.
- Tokenisation as an additional layer of security: By generating a tokenised version of the user’s identity, the system ensures that even if a quantum attacker intercepts a token, it cannot be reused or reverse engineered. Tokenisation reduces the risk of data breaches by isolating sensitive information from the data being transmitted.
- Offline operation and reduced attack surface: Biometric devices that operate offline are inherently more secure, as they do not expose sensitive data to network-based vulnerabilities. This reduces the overall attack surface, making it more difficult for quantum attackers to compromise the system and break cryptography, as the logic of creating the token cannot be followed since it happens offline.
- Layered security approach: Combining offline biometric user verification with post-quantum cryptography creates a robust security solution. Even as organisations transition to expected quantum-safe algorithms, offline biometric devices provide immediate and long-term protection against quantum threats by acting as an isolated, secure element.
The importance of strong fingerprint verification
The best solution is only as strong as the weakest link, and it has taught CardLab and our partner Fingerprints AB that there are key concerns to consider when the biometric sensor for offline verification is selected. The following needs to be considered:
Biometric algorithms
The ANSI/ISO standards for fingerprint representation consist of features that were described in the late 19th century. These features are often referred to as ‘minutiae’, which can be located manually in a fingerprint and replicated. The density of these in a fingerprint is such that for achieving good matching performance, quite a large area of skin needs to be imaged, but it also makes it possible to extract these features from other objects the user has touched or shown their fingerprint to.
To enable sensors of suitable sizes that are both low in cost and can fit into all manner of devices, a much denser feature set is required. Therefore, the standardised minutiae-based feature set is augmented by complex, more mathematical features. This enables these small sensors to achieve outstanding performance that is well suited for 1:1 verification on offline objects such as biometric cards. ‘Minutia only’ based algorithms should never be used in small-size verification devices.
Presentation Attach Detection
Algorithms for protection against fake fingerprints or Presentation Attack Detection (PAD) leverage state-of-the-art machine learning methods to analyse the fingerprint image for evidence of it being of a fake finger rather than a real one. These classifiers have the same kind of trade-off between false positives and false negatives as any discrimination into two classes (in this case, ‘real’ and ‘fake’), and the user of a biometric system will experience the combined false negatives of PAD and recognition, resulting in identity rejection of PAD.
Security
Storing templates on a secure element increases security due to the protection against physical tampering. Furthermore, encrypting templates also increases security.
Government and industry response to quantum threats
Government initiatives
Several governments worldwide have recognised the risks posed by quantum computing to national security. The European Union, for instance, has invested significantly in quantum research, with projects aimed at securing communications and protecting critical infrastructure from quantum-powered cyberattacks.
Furthermore, organisations like NIST and the European Telecommunications Standards Institute (ETSI) have collaborated on standardising quantum-safe cryptographic protocols. These efforts are critical in creating a global framework for securing information in a post-quantum era.
Industry’s role in the quantum-safe transition
Industries that handle sensitive data, such as finance, healthcare, and telecommunications, are already exploring how to integrate post-quantum cryptographic algorithms into their systems.
Leading companies are investing in quantum-safe technologies to protect their digital assets as the quantum era approaches.
In CardLab’s experience, incorporating offline biometric devices into security strategies is an essential step toward safeguarding critical information as industries transition to a fully post-quantum world. Offline identity verification is a tool to keep hackers from exploring any online vulnerabilities in the system.
Steps organisations can take now
Preparing for quantum threats should begin immediately. In CardLab’s experience, several actionable steps can help organisations mitigate risks:
- Conduct a quantum risk assessment: Evaluate the potential risks that hacking and quantum computing pose to your organisation’s sensitive data.
- Implement offline biometric authentication: Incorporating offline biometric devices for identity tokenisation into your security model provides lasting protection also while post-quantum cryptography is developed later.
- Adapt to dynamic passwords: Incorporate offline biometrically generated dynamic passwords to replace unsecured PIN codes and static passwords, eliminating ‘man-in-the-middle’ attacks, human error, and social engineering risks.
- Plan for quantum-safe cryptography: Begin migrating to post-quantum algorithms as they become standardised, ensuring that your organisation is using its best efforts to stay secure in the future.
- Adopt a layered security approach: Combine multiple layers of defence, including biometric verification & authentication, tokenisation, and quantum-safe cryptography, to protect your most valuable assets.
Future-proofing security in the quantum era
Quantum computing presents significant challenges to online security, but significant proactive steps can be taken today to mitigate these risks. Offline biometric user verification devices offer an immediate and effective solution to quantum and AI deepfake threats by combining secure, offline operations with tokenised identity verification.
As quantum computing advances, it is critical for organisations, particularly within the European Union, to adopt quantum-safe technologies and begin transitioning to a secure, quantum-era infrastructure.
By combining biometrics, tokenisation, and quantum cryptography, we can ensure that our systems remain secure, even in the face of this transformative new technology, which offers substantial benefits while introducing new threats that must be managed with foresight.